Enterprise-Wide IT Architecture (EWITA)
0/03/01
_______________________________________________________
The EWITA newsletter
Going out to a list of 280
Architects
Welcome
to the latest issue of the Enterprise-Wide IT Architecture
Newsletter!
Supporting the
Enterprise-Wide
IT Architecture (EWITA) web
site at http://www.ewita.com/
Prior
newsletters <here>
------------------------------------------------------
3. Technical Site TechRepublic
5.
We Have Mail! "looking for a reference architecture" Jonas Colmsjo, Leon Olson, Steven
van 't Veld
6.
We have Mail Two!
"tool alternatives analysis" George Brundage
7.
Announcement
I need Help,
between work, and this newsletter, I do not have sufficient time to generate
new content each time.† So if you have a
favorite web site or a white paper languishing on your C: Drive, send it to me.† Get published!† Each of us has something to contribute to this community, a
simple process, a procedure, or a white paper that you have used effectively
can be of additional use to others.† You
can get some pretty good exposure for your organization by publishing in this
newsletter.† Send contributions to
David McAfee
Contributors
for this issue are:
Chang,
Russell <mailto:rchang@experio.com>
†Steven van 't
Veld <Steven.van.t.Veld@AIM.nl> http://www.AIM.nl/
Jonas Colmsjo <jonas@colmsjo.f2s.com> www.colmsjo.f2s.com
Leon Olson <76243.3006@compuserve.com>
George Brundage <George.Brundage@cio.treas.gov>
And the gang at Employment
Development Department (State of California)
No, we are not unique! Some Pointers to state levels
of architectures (with some to counties and cities):
In an attempt to see what
was out there (on the web) for Enterprise Architectures I did a series of
searches on the following key words: Enterprise Architecture, Technology
Architecture, Enterprise-Wide IT architecture and various other key words it
the address suffix of .us.
This did NOT find all the
appropriate sites but I did get over 1000 hits from the following states: AK, AR, AZ,† CO,
CT, DE, FL, GA, IA, IN, KS, KY, LA, MA, MD, ME, MI, MN MO, MS, MT, NC, ND,
NE,† NJ, NV, NY, OH, OR, PA ,RI, SC, TX,
UT, VA, VT, WI, WY.† I refined the
number of sites to about 250 table entries, of which I have not had the
opportunity to refine the Wisconsin and Wyoming entries yet.† These last few will be validated over the
next couple of weeks.
Arkansas, Connecticut, the City of
Indianapolis, Kansas, Kentucky, Massachusetts, Montgomery County in Maryland,
ME, Minnesota, Montana, North Carolina, Nebraska, New Jersey, Ohio, Oregon,
Utah, and Virginia all have web resident Architectures.†† The other states are in the process or at
least appear to understand that EA is necessary.† It is noteworthy, that the primary type of EA is that style sponsored
by MetaGroup.† This Pointer list is
about 500k bytes, the pointer list on the EWITA
site, just go there and select LINKS
Extracted from the
CA/EDD/BDA, request full access to the BDA at CA/EDD Complete
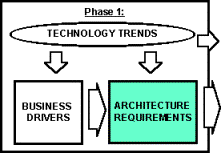
Architecture
Technology
Trends
|
|
The technology trends are widely recognized forces or
directions of change in the IT industry. These trends identify the most
important technology indicators impacting the organization and the enterprise
architecture. The Architecture will utilize trends to frame the development
of the technical architecture in the context of current technology and to
understand the impact of technology on the organization's business drivers
and architecture requirements. The Archtiecture team ranked these trends by decreasing
importance to organizationís business drivers and the Architecture. |
Network Centric Computing. The need to share information
efficiently with customers and partners, as well as internally, will cause
electronic document handling, electronic commerce, automated workflow and
collaborative computing to continue increasing dramatically through 2001.
Intranets and the Internet will become the de-facto standard delivery
mechanisms to enable information sharing and collaboration. These developments,
along with the distribution of computing services (i.e. client/server
applications), will increase the demand for network connectivity and
communications bandwidth by up to 300%. This trend elevates the importance of
the network and makes it a critical factor in the success or failure of an
organizationís business processes.
Resource Challenges. Shortages in personnel, time, and
outsourcing resources will drive 3%-4% monthly IT cost increases through 2001.
Government organizations, unable to keep pace with skyrocketing salary
requirements due to flat or declining budgets, will be acutely affected.
Organizations that have difficulty attracting and retaining IT professionals
cannot afford to invest resources into niche oriented, leading-edge products.
To address this situation, successful organizations concentrate on using market
dominant providers for their technology solutions, thus ensuring a broader
labor pool.
Internet/Intranet. The Internet and its capabilities
are becoming a universal business communications medium. They will drive
standards for network computing, collaborative computing and electronic
commerce. During 2001/2002, development using these tools will focus
increasingly on legacy/enterprise application integration and mission critical
(e.g. systems that require a high level of reliability, availability,
scalability) Intranet/extranet applications.
Data Warehouse. The need to accelerate
decision-making causes organizations to put operational data from the
lines-of-business into data warehouses that provide enterprise-wide views of
information. Powerful, yet easy-to-use, GUI analysis tools in the hands of decision-makers
will provide them with immediate access to key information. Information from
the data warehouse will continue to be electronically disseminated to knowledge
workers within the organization, external business partners and customers.
Security. As organizations increase
information sharing and access to data for customers and partners via the
Internet, the complexity of securing information is increasing. The lack of
encompassing security products/standards will hinder the ability of a single all
encompassing security solution. This will cause selection and implementation of
various enterprise-wide security solutions based on specific local factors. A
demand for single sign-on, (one user log-on Id.), will drive development of
security infrastructure with auditability, authentication (smart cards), and
strong identification (fingerprint, voiceprint , etc.).
Total Cost of Ownership (TCO) of IT. Because of the rising costs of IT
support services and personnel, organizations are over engineering their
technology infrastructure (hardware, software and networks). By 2001,
successful organizations will emphasize the use of standards and "best
practices" to reduce integration complexity rather than optimize the
performance of individual infrastructure systems to reduce TCO.
Technology Price/Performance Curve. Innovations in the technology
industry will continue to lower price/performance curves. Computer processing
speeds will continue to double every 18-20 months. Network transmission
technologies promise to deliver dramatic increases in network transmission
capacity (bandwidth) and lower costs. Costs of computer memory and the
electronic storage of data are decreasing rapidly.
Mobile Connectivity. The demand for information by
mobile users is increasing as the ability to provide personalized customer
service (at the point of customer contact) becomes a strategic competitive
advantage. Successful organizations design infrastructures with remote access
in mind. This drives organizations to develop enterprise-wide remote access
solutions. The need for mobile connectivity will help increase the use of
wireless technologies 20%-30% annually.
Systems Management and Support. Growing personal computer use,
dramatically increasing network traffic levels, Intranet applications and
expanding complexity of IT systems will drive cost increases related to systems
and personnel support services. Organizations are implementing enterprise-wide
system management solutions and service-level agreements to control these costs,
and also to improve reliability, network availability and disaster recovery.
Client/Server Application
Development. The
Client/Server model of distributed systems will continue to grow. In this
model, the dominate industry trend is to separate, at minimum, the data access,
business-logic and presentation parts of the application. Centralized legacy
systems will continue to be a primary service delivery for high transaction
volume production-oriented applications. However, increasingly, legacy data
will be interfaced into new client/server and web-enabled browser-based
applications.
Organizational Dual Discipline
Proficiency. IT has
become an integral component to nearly all business processes. The information
content of products and services is becoming a primary critical success factor
in most organizations. This forces organizations to recognize the impact and
importance of cross-training IT professionals and business managers. IT
professionals have a solid understanding of the drivers and requirements of
their business customers. Business managers are versed in current technology
issues and trends that affect their organization.
Application Development Tools. Stand-alone tools used for limited,
specific purposes lose market share as the environment in most tool categories
is consolidated around integrated tools from a few, significant vendors. Legacy
system support and application maintenance will continue with most of the same
tools as used today.
Buy vs. Build. Buy for competitive parity, build
for competitive advantage. Through 2001, organizations will want to buy
commercial applications before they build functionally equivalent versions
because of time-to-market pressures. Additionally, the rising cost of IT staff
has increased the time to recover the costs of applications developed in-house.
Outsourcing. Organizations are increasingly
utilizing external providers for selected IT services. The areas organizations
most commonly outsource are:
Data Center Services and Network Services (wide-area
networks and remote access)
Application Maintenance (legacy code updates/minor
enhancements)
Implementation of Package Applications and Custom
Application Development
Distributed IT Services (help desk and PC
asset management).
Technical
Site:
Here is a site for IT professionals, they have a lot
of tools for general consultants:
From the
Site:
Welcome to TechRepublic,
the only Web community created for IT pros by IT pros.
TechRepublic provides the information you need to succeed no
matter what your IT role. Take a look around and discover the personalized
information, news, and career advice we've put together just for IT pros like
you.
- Personalized Content: our technology delivers just what you need,
each time you visit.
- Technical Q&As and
Discussions: talk to other IT
pros about what keeps you up at night.
- Free Downloads: forms, templates, checklists, Gartner product
analysis, and more.
- Job Directory: find your IT dream job.
- IT Vender Directory: search for and locate the specific IT resources
you need.
- Free E-newsletters: get regular updates on IT topics from software
tips to IT support
Comments:
This is a free membership site with sections for the
CIO, IT Manager, Network Administrator, Developer Support and IT Consultants.
Here is a set of models for the development of a
federal level architecture based on the Zachman models.
The products associated with the Federal Enterprise
Architecture Framework
(FEAF) Pilot are at
http://www.itpolicy.gsa.gov/mke/archplus/cmodel.htm
These products are primarily Mitre Grants Products and include
Activity Model (OV-5) (PowerPoint) November 27, 2000
Activity Model Data Dictionary (Word) November 27, 2000
Grants Activity Hierarchy Chart November 27, 2000
Operational Node Connectivity Diagram (PowerPoint) December 19, 2000
Top Level Operational Node Connectivity Diagram (Word) December 19, 2000
And Ptech Grants Products (Ptech Framework)
Ptech FEAF Grants Target
†Ptech Meta Models
Ptech FEAF Meta Models 11/22/00.
Here are site listings† for many publications for those of you who like online reading,
both newspapers and magazines.
http://www.siteone.com/papers/mags.htm
http://www.siteone.com/papers/intern.htm
http://www.siteone.com/papers/nation.htm
From DCI:
The Government Enterprise
Architectures Conference
http://www.dci.com/brochure/eacdc/schedule.asp
From Computer World:
The following contain a
impressive list of white paper pointers
http://itreports.computerworld.com/cw1
Developers of Enterprise
Architectures:
The consulting firm that the State of California,
Employment development Department used to assist in the development of their
Business Driven Architecture was purchased and renamed to Experio Solutions, I
received this announcement from Russell Chang (rchang@experio.com) who worked with me on
the project.†
Announcing Experio
Solutions
Experio
Solutions is a new name but we are not a new company; we are still the same
knowledgeable and experienced group we have always been.† We are the former Grant Thornton e-Business
Consulting Group, which has been in operations for more than 20 years.† On November 1, 2000, we became Experio
Solutions, a company of Hitachi which is one of the world's leading global
electronics companies.† We provide
solutions, knowledge and experience to mid-size and Fortune 1000 companies in
areas such as Enterprise Architecture (EA), e-Business strategies and
technologies, customer relationship management, enterprise resource planning
and supply chain management.† Our
client-contact consultants are seasoned professionals who average more than 7
years of business experience so they have the necessary knowledge and skills to
execute engagements on time and on budget, delivering client satisfaction the
entire way.
Throughout
this transition, the Experio Solutions EA practice has continued to offer the
industry leading EA consulting services to our clients.† With our comprehensive and proven
methodology based on real world client experiences and our ongoing team of
experienced EA project consultants, we set the industry standard with our
approach for assisting clients in the development of an EA.† We strive to help you achieve tangible,
bottom line results.† Our
business-driven, consensus-based approach gets the right people involved in the
beginning of the process to ensure that the effort has the necessary support.† We utilize a results-oriented, phased
approach that stresses knowledge transfer between Experio and client
staff.† This ensures that your team will
be able to successfully continue driving your EA process after our time in the
project room is over.
We are Experio Solutions.† Go with the
experienced leader.
We Have
Mail!
From: Jonas Colmsjo <jonas@colmsjo.f2s.com>
Sent: Wednesday, February 21, 2001 5:08
AM
Subject: [EWITA - Enterprise-Wide IT
Architecture] Reference Application Architecture
> I am looking for a reference
architecture for an application architecture.
> It should cover typical support systems for an enterprise, i.e CRM, ERP,
> HR systems with short descriptions of the applications in each system.
> Does anybody know of any standard, de facto standard application
architectures
> that could be used for this?
> /Jonas
> Jonas Colmsjo
> jonas@colmsjo.f2s.com www.colmsjo.f2s.com
--------------------------------------------------------------------------------------------------------------------------------
----- Original Message -----
From: Leon Olson <76243.3006@compuserve.com>
Sent: Tuesday, February 27, 2001 2:57 PM
Subject: [EWITA - Enterprise-Wide IT
Architecture] Reference Application Architecture
> Dear EWIT Staff:
> Please let me know if you find such a web site?
> As I understand your question:s 'where do I find the
> Enterprise Enterprise Architecture?'
> My question is? How many Enterprise Architectute(s)
> are there? You have mentioned a new one. Thanks.
> I suggest there should be what you propose, but that
> is only a start, e.g., 'The Funding Enterprise' Architecture.
> You mention the Support Enterprise Architecture, there
> are many more.
> If you would like to examine these Enterprise Architecture(s)
> please reply and we can discuss them and why..
> Thank you for your time.
> Sincerely,
> Leon Curtis Olson
> Enterprise Architecture
> Users Group
> Member At Large
> G-M: 12203 Cedarbrook Lane
> Laurel, MD 20708
> V-m: 301.483.9643 (EST 9a-4p)
----------------------------------------------------------------------------------------------------------------
----- Original Message -----
From: A/I/M - Steven van 't Veld - drs Marleen Olde Hartmann <Info@aim.nl>
Sent: Wednesday, February 28, 2001 4:15
AM
Subject: RE: [EWITA - Enterprise-Wide IT
Architecture] Digest Number 29
> Hi Jonas,
> This is a simple question with a not-so-simple answer.
> An application architecture is part of the IT-architecture within the
> architecture of the information infrastructure of the organisation. When
> looking at the application architecture you have to distinguish between
the
> current situation and the future situation.
> Looking at a current situation you look at what you have. This is usually
a
> legacy of interrelated applications which is difficult to portray and, in
my
> opinion, not standardisable. The problem is usually the grouping of the
> applications you have to create an architecture you can
"handle". Another
> problem is the number of interfaces between the applications and with the
> environment.
> Looking at the future situation, and I mean way ahead, you can envision an
> "ideal" application architecture. By introducing some
groundrules it is
> fairly easy to build it up. Say, for instance, a groundrule is that you
only
> identify structured data ("databases"), unstructured data
("documents") and
> "loose" data (the data that is not managed but floates around in
directories
> etc). If you make this the Data Architecture you can put functionality on
> top. This functionality will become your application architecture.
> Just looking at ERP, for instance, doesn't do the trick. ERP will do at
most
> 30 to 40% of your processing, no more.
> Going some steps further introducing an application architecture and a
data
> architecture is not the main concern. What you want is an (enterpise)
> information architecture. Here we find the conceptual models of
> functionality and information. Here you will find everything just once.
> Relating your application and data with your functionality and information
> will show you where the duplicates are. The key is here is to separate the
> notions of Information and IT. IT is used for solutions. Information is
what
> an organisatioon wants to own.
> With regard to the conceptual models there are standards available. I do
see
> some good practices, but hardly any standards on application architectures
> themselves because they are usually specific to organisations.
> I do hope this helps you out
> Met vriendelijke groet,
> Steven van 't Veld
> Principal Consultant en (enterprise) information architect
> Architectuur, Informatie & Management (A/I/M) bv.
> E-mail: Steven.van.t.Veld@AIM.nl
> Homepage: < http://www.AIM.nl/>
----------------------------------------------------------------------------------------------------------------
We Have Mail Two:
A
question from the Federal Architecture area
From: George Brundage <George.Brundage@cio.treas.gov>
Sent: Wednesday, February 28, 2001 5:52
AM
Subject: Architecture Items - Tools,
February 28, 2001
> I would like to get your comments on
the following tool alternatives:
> Alternatives Analysis
> Alternative 1: Select a single tool, and through the tool's meta-models
> enforce the rules and constraints associated with the products developed
by
> the bureaus.
> Alternative 2: Select a standard set of architecture tools. These tools
> will be used to enforce the rules and constraints associated with the
> products or diagrams. Again, enforcement will be through standard
> meta-models. (Building diagrams in two tools will complicate the analysis.
> Some tools may be better for certain products than others; for example, I
> was told that the Operational Event/Trace Description and the Systems
> Functionality Description, which are both in the DoD and Treasury
> architecture frameworks, are best developed in UML.)
> Alternative 3: Others might argue that a standard tool(s) is not possible,
> and suggest that the bureaus use whatever tools they want as long as they
> produce the representations in accordance with the TEAF. The work products
> should be accessible to everyone in the agency; therefore, the products
> must be put in some kind of common form (e.g., html, pdf) or delivered to
> an agency common repository which would be accessible to everyone.
> Otherwise, some of the work products may end up in some softcopy format
> that you must purchase the tool in order to read. (A repository approach
> might allow analysis to be done across products from multiple
> architectures; although, this analysis will be far more complicated than
in
> alternatives 1 and 2. Some would argue that using html and pdf
> representations is no better than paper representations.) Others have
> suggested that the vendors save to a standard format (other than html and
> pdf); although it is unknown whether this is likely to happen.
> What is a meta-model: The meta-models define the types of analysis that
> can be done. Meta-models enable forms, queries, and reports to
"navigate"
> the diagrams. So for example, if you wanted to see for an operational node
> all of its activities, all the needlines it sends, all the ones it
> receives, and/or any other instances of another object from another
> diagram, this could be done because the meta-models have defined these
> associations and instances of these objects have been created. <toc>